Browser Isolation: Fail-Safe Protection Against Phishing and Malware Attacks
We are permanently at risk of malware infection because of the way in which browsers work
Right now, cybercrime is a big problem for any business. And malware and phishing attacks are a big part of that problem. To date, businesses have defended against phishing attacks with mandatory cybersecurity awareness training. But while employee training is essential for reducing an organisation’s vulnerability to phishing scams, can we expect that it will eradicate the problem entirely? The data says not.
A 2018 study of email phishing attack simulations found that trained graduates continued to be taken in by phishing scams at a rate of about 9%. Even after the training, we’re still getting stung. It’s a tough call to make, but perhaps we shouldn’t be banking on perfection. Perhaps instead we should be expecting and preparing for, the occasional slip-up. In the case of phishing and ransomware attacks, we can prepare for failure with using browser isolation.
So what is browser isolation? And how can it help you against phishing?
Browsing the web is a risky business. Every time that we do, there is a chance that we will become infected with malware such as ransomware, or one designed to steal our passwords. But there is a way to ensure that this NEVER EVER happens.
It’s called isolated browsing.
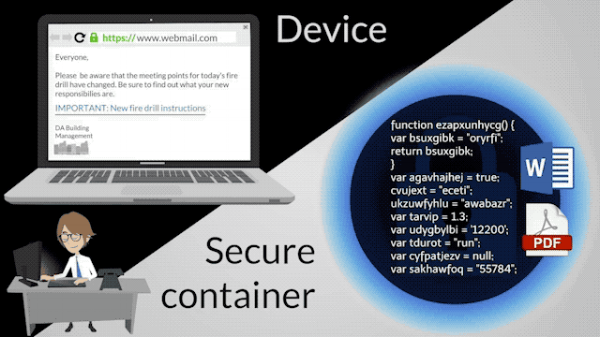
When we implement isolated browsing, we effectively move all our browsing activity into a purpose-built, secure and private environment in the cloud. This change means that the content that we consume online is kept private and it is impossible for us to become infected as a result of browsing the web.
But what’s wrong with my conventional browing method?
We all use the web, and most of us have a conventional browser setup.
In conventional browsing, a direct connection is made between a locally installed browser and the web. Direct connections are problematic because of the way in which browsers work. When we make a direct connection, the contents of the page or document are downloaded and executed locally on the device.
This becomes a problem when the content that we have downloaded is malicious. If that’s the case, then the device that we are using may become infected.
In conventional browsing, we download third party content and code to our device (risky)
The location of your browser can make the difference between being safe and getting malware attacks
The browser is always going to be a primary entry point for malware into any business. It’s an open door for attackers.
The only way to absolutely 100% guarantee that we won’t become infected by web-borne malware is to move the browser
This change of location is the basis of browser isolation. When we implement browser isolation, all browser-based activities are physically moved away from the device that we are using and into a secure container in the cloud.
To defend against web-borne malware, we must move all browsing activities off our devices.
For the user, the experience is much the same. But under the covers there’s one key difference - no potentially dangerous web content is ever downloaded to the device.
When we switch to isolated browsing, we cannot get infected even if we trigger a virus
If we take a wrong turn on the web and trigger an infection, there are no negative consequences. The virus is held offsite, within the secure container. And the device, and the business, remains unaffected.
For some businesses, ransomware is an accident waiting to happen
Getting stung by ransomware can have multiple negative outcomes
The frequency of attacks is growing. And the consequences of falling victim remain severe. In some cases, the business never recovers.
60% of small businesses that become infected with ransomware will close within 6 months
Browser isolation provides immediate protection from web-borne threats for those organisations whose cybersecurity training program is still in the planning stage. And adds a fail-safe for those organisations that already have a program in play.
Browser isolation helps all businesses regardless of the status of their training program
No business can operate without the web. But conventional web browsing is risky. In the past, we’ve addressed the problem by limiting access to risky applications, but this often doesn’t go down too well.
Isolated browsing is a quick, easy and cost-effective solution to the threat of ransomware
By switching to isolated browsing, we have a quick, easy and cost-effective way to eliminate the risk of web-borne infections. And ensure that everyone gets the access that they need.
Isolated browsing is relatively new, with adoption rates at the start of the year as low as 5%. But isolating the browser is the ONLY 100% guaranteed way to ensure that a business never gets infected from web-borne viruses. Given the ever-present and growing threat of ransomware (and newcomers such as cryptojacking) and the severity of falling victim, we can expect to hear much more about isolated browsing in teh not too distant future.
When we switch to isolated browsing we completely eliminate the risk of becoming infected by web-borne malware
So how can you implement isolated browsing?
Right now, online privacy and security are key (and growing) concerns for us all. But up until now these goals have been difficult to attain. By making the quick and non-technical change to isolated browsing, we ensure that:
Our online privacy is respected
We can never become infected by any web-borne malware
The integrity of our computer, data, finances and identity all remain 100% intact
Check the videos below to learn more. And remember to hit the Share button top right of the video!